ENDPOINT SECURITY SOLUTION
Endpoint Protection
The use of laptops, tablets, mobile devices and other wireless gadgets connected with corporate networks creates vulnerability paths for security threats. Endpoint security solutions attempts to ensure that such devices follow a definite level of compliance and standards.
Usually, endpoint security is a client/server based system that consists of security software, located on a centrally managed and accessible server within the network or in the cloud, in addition to client software being installed on each of the endpoints (devices), as well as on the network servers. Central management server authenticates logins from the endpoints and updates the device policies and software when needed.
Endpoint security software differs by vendor, but at minimum include antivirus, antispyware and a host intrusion prevention system (HIPS).
Sophos Endpoint Protection
security by protecting workstations, laptops and servers against known and unknown threats. It delivers integrated protection against security threats, including viruses, spyware, trojans, worms, adware and potentially unwanted applications (PUAs). It offers protection to most of today used operating systems such as Windows, Mac, Linux and Unix.
Sophos Endpoint Protection relies on SophosLabs™, global network of centers of threat analysis, as well as 25 years of experience and expertise in the IT security field, to provide a consistently high level of security.
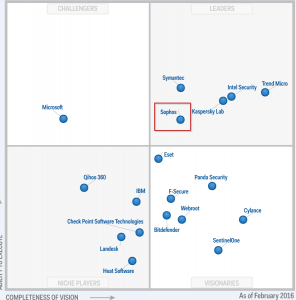
Sophos Endpoint Protection solution is classified as a leader in Gartner’s Magic Quadrant for endpoint protection solutions for the year of 2016:
Gartner Magic Quadrant for Endpoint Protection Solutions
Sophos Endpoint Protection software bundle fully integrates the following components:
• Anti-virus. Sophos Antivirus detects, blocks and cleans up known or unknown threats, including virus, spyware, adware, and potentially unwanted applications. It also monitors applications launched on the endpoints, removable devices and data that are forwarded or transmitted.
• Host Intrusion Prevention System (HIPS). HIPS dynamically analyze the behavior of programs running on the system in order to detect and block activities which appears to be malicious.
• Client Firewall. Monitors application behavior, hardens computers and protects networks against Internet worms, hackers and infections transmitted through compromised computers.
• Application Control. Monitor and prevent users from running applications that may affect productivity or network performance in an enterprise environment. Application Control can also enforce company policies as well as reduce security risks.
• Device control. Managed access to removable media and mobile devices. It enables to define which computers have access to specific removable devices. Device Control can stop data loss by not allowing using specific devices and also spreading of malware which uses removable media to infect computers. Devices that can be managed are:
• Secure removable storage.
• CD and DVD devices.
• Infrared devices.
• Wi-Fi devices.
• Bluetooth interfaces.
• Web Protection. Controls internet use for users by blocking access to unauthorized and infected web sites. Also provides category-based web filtering that is enforced on endpoints when they are both on and off the corporate network.
• Data Loss Prevention (DLP). Prevents data leakage of sensitive information. SophosLabs have developed many pre-configured CCLs (Content Control List), such as credit card numbers, bank account numbers, social security numbers, addresses, phone numbers, postal codes defined by countries such as France, England, Germany, USA, etc...If a desired format is not predefined, custom content rules can be defined using wizard provided for this purpose.
• Patch Assessment. Checks for security patches from Microsoft and other vendors and keeps informed about the risks level, allowing to focus remediation efforts on the most exposed environments.
• Tamper protection. Prevents unauthorized users and known malware from uninstalling Sophos security software or disabling it through the Sophos Endpoint Security and Control interface.
Key components of Sophos Endpoint Protection suite are:
• Management console – Sophos Enterprise Console.
• Endpoint software – Endpoint Security and Control (Sophos Anti-Virus, Client Firewall, software to handle updates and messaging, etc.).
• Management database – Store information about the configuration of endpoint computers.
• Management server and management service – Handle communications between the console, the database, and the endpoint computers
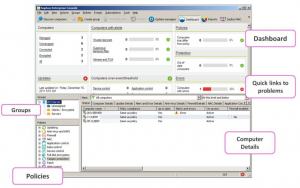
Sophos Enterprise Console
Sophos Enterprise Console is used to deploy, update, configure and monitor clients, with centralized administration of all Sophos Endpoint Protection components on simple and complex networks. Sophos Enterprise Console helps customers manage all the security features included in Endpoint Protection. SQL Server is used to store data for the application.
Enterprise Console supports management of Windows, Linux, Mac OS X, UNIX and virtualized machines. It allows administrators to:
• Discover all computers on the network.
• Deploy Sophos to endpoints.
• Create and assign policies to be enforced on endpoints.
• View/Inspect the current status of Sophos installations.
• View and resolve alerts and errors centrally.
• Force immediate scans or updates on the endpoint.
• Generate reports.
Sophos Endpoint Protection software bundle fully integrates the following components:
• Anti-virus. Sophos Antivirus detects, blocks and cleans up known or unknown threats, including virus, spyware, adware, and potentially unwanted applications. It also monitors applications launched on the endpoints, removable devices and data that are forwarded or transmitted.
• Host Intrusion Prevention System (HIPS). HIPS dynamically analyze the behavior of programs running on the system in order to detect and block activities which appears to be malicious.
• Client Firewall. Monitors application behavior, hardens computers and protects networks against Internet worms, hackers and infections transmitted through compromised computers.
• Application Control. Monitor and prevent users from running applications that may affect productivity or network performance in an enterprise environment. Application Control can also enforce company policies as well as reduce security risks.
• Device control. Managed access to removable media and mobile devices. It enables to define which computers have access to specific removable devices. Device Control can stop data loss by not allowing using specific devices and also spreading of malware which uses removable media to infect computers. Devices that can be managed are:
• Removable storage.
• Secure removable storage.
• CD and DVD devices.
• Infrared devices.
Sophos Enterprise Management Console
Today’s malware is difficult to detect, difficult to remove and difficult to recover from. Traditionally, antivirus software relies upon signatures to identify malware. This can be very effective, but cannot defend against malware unless samples have already been obtained, signatures generated and updates distributed to users. Because of this, signature-based approaches are not effective against zero-day viruses.
Signature-less threat and malware detection solutions protects again against zero-day attacks, Advanced Persistent Threats (APTs) and crypto-ransomware that can evade traditional, signature-based endpoint products.
Sophos Intercept X
Sophos Intercept X is Next-Generation Anti-Exploit, Anti-Ransomware, and Root Cause Analysis that adds next-generation signature-less technologies on top of your current endpoint security to give you complete layered protection.
• Protect Vulnerable Software. Anti-exploit technology stops threats before they become an issue by recognizing and blocking common malware delivery techniques, thus protecting endpoints from unknown threats and zero-day vulnerabilities.
• Effective Ransomware Detection. CryptoGuard technology detects spontaneous malicious data encryption to stop ransomware in its tracks. Even if trusted files or processes are abused or hijacked, Sophos Endpoint Protection will stop and revert them without any interaction from users or IT support personnel. CryptoGuard works silently at the file system level, keeping track of remote computers and local processes that attempt to modify documents and other files.
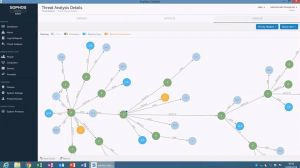
• Root Cause Analysis. Identifying malware and isolating and removing it solves the immediate problem. But do you really know what the malware did before it was removed, or how it was introduced in the first place? Root cause analysis shows all the events that led up to a detection. You’ll be able to understand what files, processes, and registry keys were touched by the malware and activate your advanced system clean to rewind time.
• Add Next-Gen Protection to Your Traditional Security. Sophos Intercept X compliments existing anti-malware and antivirus implementations delivering powerful next-gen anti-exploit and anti-ransomware protection traditional products lack. By eliminating the attack vectors which traditional solutions don’t block, Sophos Intercept X helps to harden your security posture and increase resilience.
Sophos Intercept X Root Cause Analysis
Sophos Clean
Sophos Clean signature-less technology uses progressive behavior analytics, forensics, and collective intelligence to discover and remove zero-day threats, trojans, rootkits, ransomware, and other polymorphic malware. This solution is ideal for companies not using Sophos Endpoint who have a malware infection or who would like a second opinion on how their current endpoint security is working.
Instead of searching for typical static malware attributes, Sophos Clean looks for unethical behaviors. It's much harder for malware authors to radically change the manipulative behavior of their malware than it is to change its static properties. The clean up capability removes the immediate threat and unpicks all the system changes, such as files written and registry changes, restoring your system to its pre-infection state. By combining forensic, behavior, and collective intelligence, Sophos Clean is the single most effective solution to combat new and resilient malware.
How does it work:
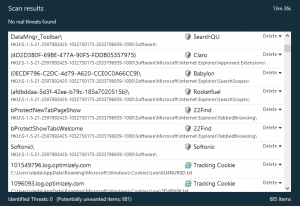
• Second Opinion Scan - Instead of relying on signatures, Sophos Clean gathers actionable intelligence and examines the collected information. This signature less approach allows the scanner to discover which files act and look like malware.
• Discovery - It’s designed to discover viruses, trojans, rootkits, spyware and other malware on up-to-date and fully protected computers. It searches for early-life and next-generation malware; the kind of malware that doesn't yet have a detection signature.
• Fix It - Sophos Clean removes persistent threats from within the operating system and replaces infected Windows resources with the original, safe versions. Reinfection attempts are proactively blocked until threat remediation is completed.
Sophos Clean Scan Results