NETWORK SECURITY SOLUTIONS
Unified Threat Management (UTM)
About UTM Security
Unified Threat Management (UTM) is a term used to describe a category of security solutions which integrates range of security features into a single appliance. UTM represents the evolution of traditional firewall product in a solution that is able to perform multiple security functions within a single system. It provides a broad, integrated and high-performance protection against dynamic security threats, while simplifying IT security infrastructure.
UTM consolidate a wide range of basic network security functions such as Firewall, IDS/IPS (Intrusion Detection System/Intrusion Prevention System), Gateway Antivirus/Antispam, VPN (Virtual Private Network), Web Filtering, Bandwidth Management and so on.
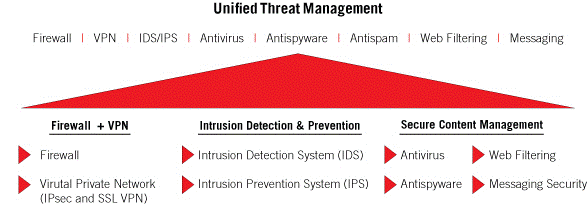
UTM consolidation of network security functions
Advanced security features, that some of UTM manufacturers integrate into their solutions may include Application Control, Web Application Firewall, Reverse Proxy, Wireless Security, DLP (Data Leak Prevention), etc.
Considering the fact that all modules are integrated within a single appliance, this leads to their better connectivity and higher throughput of the entire system, compared to the traditional concept which combines independent, multi-vendor products to achieve the same result.
The primary market for UTM are small (less than 100) and medium (between 100 and 1000 employees) environments, so called SMB (Small or Midsize Businesses). Such environments generally do not have high budgets allocated for IT security projects and usually lack IT staff highly specialized and trained in the field of network security. UTM solution for SMB segments provides advantages both from financial and technical point of view:
• With the purchase of only one solution from one vendor, company will cover almost all of their network security needs. In addition, most UTM manufacturers provide customers with the flexible licensing options, where company can buy only those functional modules that are really necessary for their IT security infrastructure.
• Administration and configuration of all security features is done from a single administrative point, usually via GUI (Graphical User Interface) administrative console.
• Tracking, monitoring, updating and upgrading is done only over a single system/solution.
• Reporting about the status and statistics of all security features and modules can be combined into a single report. Centralized logging of all security events makes it easier to achieve regulatory compliance with the standards that are required in certain industries (PCI-DSS, HIPAA, GLBA, SOX…).
• There is only a single line of support. In case of technical or licensing questions, as well as any functional problems, customer communicates only with a single vendor support.
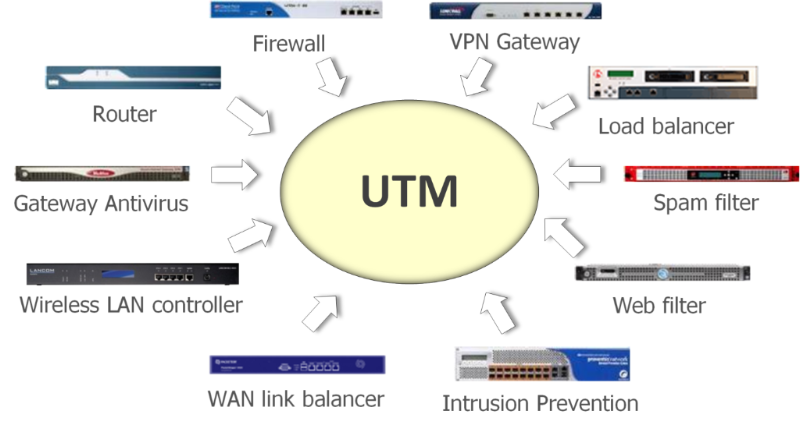
UTM as a substitution for individual network security solutions
Sophos UTM Solution
Sophos UTM combines the very latest technologies for email, web, network and endpoint security to create highly manageable, all-in-one solution that is cost-efficient and easy to operate. For every Sophos UTM appliance, an Essential Network Firewall license is available free of charge. It activates the basic functionality with the fundamental security functions to protect company networks. These can be expanded through flexible, optional security subscriptions of Sophos UTM:
• Network protection. Flexible setup of site-to-site and remote access VPN connections, routing, IDS, IPS, next generation firewalling, and protection against denial-of-service attacks, sophisticated worms and hacker exploits through a fully integrated intrusion protection system.
• Email protection. Secures corporate email from spam and viruses, and keeps sensitive information from ending up in the wrong hands.
• Web protection. Web browsing filtering to protect employees from web threats and to control how they spend their time online.
• Web Server protection. Intelligent reverse proxies harden web servers and web applications to protect them against modern attacks and data loss.
• Wireless protection. Makes running secure, reliable wireless networks simple.
• Endpoint protection. Easily deploy Sophos antivirus software to computers and set policies to keep users safe.
• Sandstorm. Powerful, cloud-based, next-generation sandbox technology that quickly and accurately detect, block, and respond to APTs and zero-day threats.

Sophos UTM modules
Sophos UTM’s unified management console is easy to administer and offers comprehensive functionality of enterprise solutions.
Sophos UTM administrative console
Sophos UTM comes with the following industry certifications:




ICSA Labs Firewall certification
Common criteria EAL 4+
IPv6 ready
VmWare ready
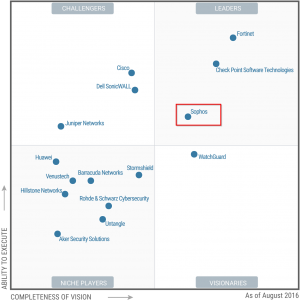
Sophos UTM solution is classified as a leader in Gartner’s Magic Quadrant for UTM solutions in the year of 2016:
Gartner Magic Quadrant for Unified Threat Management
WiFi networks are a requirement for doing business today. Business WiFi networks are more complex than home WiFi networks. They must support visitors and contractors as well as employees – all of whom need varying levels of access. Businesses also need to enable employees to access the WiFi network with their personal devices. Without proper access controls anybody can connect to the network, putting sensitive data at risk.
Consumer access points are insufficient for business needs. They have to be set up individually and often offer limited or no support for business requirements, such as virtual private networking. Businesses also risk data loss by not managing guest access. Business WiFi solutions offer a number of options for different deployment scenarios. Access points can be placed on a desktop, or wall or ceiling mounted, depending on what coverage is required and how the office space is set up. There are even options that are suitable for outdoor use to provide coverage for loading bays and similar areas, which may be more exposed.
Sophos Wireless Protection
Sophos Wireless Protection enables secure and reliable wireless access by using Sophos UTM or Sophos Central Cloud as a wireless controller to centralize WiFi management and security. Sophos access points are automatically set up and configured by the controller.
• Installs fast with automatic setup and configuration. Multiple wireless Access Points (APs) can be setup within minutes. They require no local configuration and will simply find the controller, retrieve their IP address via DHCP, and import the configuration. Devices automatically appear in the administrative interface where can be manually activated.
• Creates reliable networks for all areas. Sophos access points support a variety of deployment scenarios. They include models for desktop/wall mounting such as the entry-level AP 15 and the enterprise-grade AP 55 and AP 100. The AP 15C, 55C and 100C are smoke-detector style ceiling-mount and the AP 100X is suitable for outdoor use.
• Provides guest WiFi and BYOD access. Sophos provides secure, easy-to-manage guest access out-of-the-box, without extra appliances, licenses or complex configuration. Guest experience can be tailored to suit business needs. It is possible to set bandwidth limits and content filtering as well as customizing the login page and vouchers to strengthen a company brand.
• Secure wireless and integrated network protection. To prevent unauthorized access the most advanced encryption and authentication standards available are supported, including WPA2-Enterprise in combination with IEEE 802.1X (RADIUS authentication). Sophos APs forward wireless traffic to the UTM, giving wireless clients the same level of security as if they were physically connected to the LAN. User authentication can be also based on their credentials from any back end server supported by UTM (Active Directory, eDirectory, LDAP...), for greater flexibility and control.
• Multi-site management and cloud scalability. One of the benefits of a cloud-managed wireless solution is scalability. Whether you have just one growing network, or multiple sites, extending Wi-Fi is as simple as adding an additional access point. With Sophos Central Cloud basic site planning tools you get a first impression of what your set-up will look like, before doing a more detailed site survey and plan.

Sophos Access Point Devices
Branch Office Security
The number of companies that have remote workers or branch offices is growing. This expansion comes alongside greater use of the internet for communication and collaboration. The IT requirements at each location can be fairly basic and IT skills at these branches often don't exist. On the other side, typical branch office environment needs often the same functionality as the head office when it comes to security — firewall, VPN, IPS, web and email security are all just as important to remote workers as those at headquarters.
Enforcing consistent network security throughout an enterprise can be challenging, especially for those branch offices with few users and no IT expertise on-site. The two primary challenges are implementing business policies and managing branch office IT.
Sophos RED
Sophos Remote Ethernet Device (RED) is a small network appliance built on the latest enterprise-class, high-speed networking platforms, designed to be as simple to deploy as possible. Its main purpose is to provide a secure tunnel from its deployment location to an Sophos UTM firewall.
Sophos RED protects branch offices and provides secure remote access. Branch office traffic is forwarded to the Sophos UTM appliance for complete security. There is no user interface on the RED appliance. It is designed to be fully configured and managed from an Sophos UTM. RED devices can be shipped to a remote site, connected to any DHCP connection to the internet, and be fully configured by a remote administrator with no prior knowledge of the site, and no need to walk local personnel through technical setup steps.
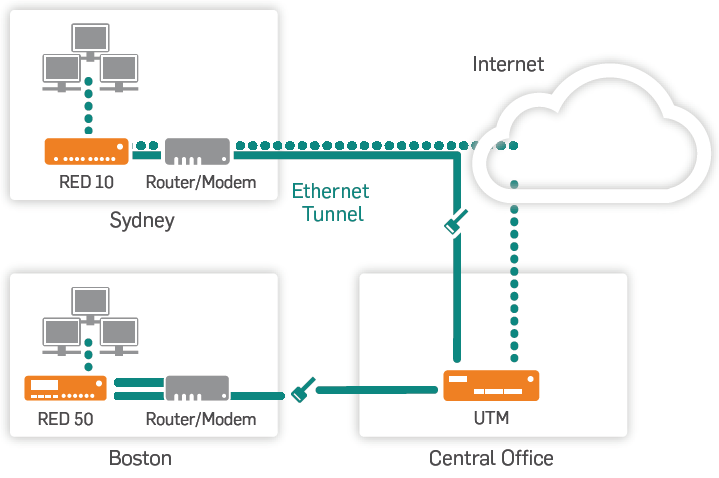
Sophos RED Deployment Scenario
Sophos RED benefits:
• Rapid deployment. RED is the security gateway that doesn’t require local set up or technical skills at the remote site. The entire configuration is done at the central office with simply entering a name and the unique device ID printed on the RED into Sophos UTM. A new configuration file is automatically created and stored with the Sophos provisioning service.
When unconfigured Sophos RED device is shipped to the remote office it should only have to be connected to the Internet cable and plugged into the wall. RED device powers up and automatically retrieves its configuration from the provision service. It then connects to the central Sophos UTM and establishes a secure Ethernet tunnel.
• Virtual Ethernet cable. Sophos RED acts like a remote network port connected by a virtual Ethernet cable to central Sophos UTM. All data sent to the central UTM appliance is protected with strong encryption. Sophos RED creates a secure Ethernet tunnel to UTM appliance using AES256 encryption and SHA1-HMAC authentication. Before it is sent across the network, data is authenticated via SSL by using trusted digital X.509 certificates.
Hardware-based AES encryption accelerates throughput rates and ensures low latency. Each Sophos RED device can provide throughput rates of more than 90 Mbps, which should be easily enough for most small office Internet connections.
• Built-in central management. Sophos UTM controls RED so there is no need to manage individual devices. Everything from configuration, logging and troubleshooting are done from Sophos UTM. No matter where the offices are, all they need is a internet connection.
Sophos RED also simplifies security policies. There is no need to create and maintain separate security policies for each branch office. One global security policy protects all remote sites.
There is no need for separate reporting tools. Built-in reporting integrates RED-connected networks, just as if they were physically connected to Sophos UTM.

Sophos RED Devices
Vulnerabilities are the holes and coding flaws that hackers exploit so that they could wreak havoc on any supposedly secure website or domain. Their malware programs will more likely gain access to a given network if they could identify vulnerabilities that the network owner neglected to find.
The main definition of vulnerability assessment is the use of different processes in order to identify, quantity and prioritize the different vulnerabilities in a system, find the holes before attackers break in and make it more robust and less exploitable.
In order to preserve the security of the computer and the network to which the computer is connected, it is vitally important that vulnerability management processes be carried out.
The process of vulnerability assessment is a key factor to improve network security. The amount of vulnerabilities that are found in a network on a daily basis are so high that more often than not, managers have to carry out large scale vulnerability tests in order to confirm all problems are rooted out of the system. The main purpose of vulnerability management is to first identify, then categorize, then remediate and finally mitigate any vulnerabilities within a system.
Secpoint Penetrator Vulnerability Scanner
The SecPoint Penetrator is a vulnerability scanning device that simulates how a hacker could penetrate a given system and reports vulnerabilities, which should then help strengthen security measures against online outlaws, cyber criminals, techno terrorists, and other malicious elements of the Worldwide Web at large.
The Penetrator can find vulnerabilities in Firewalls, Routers, Linux, Windows, Mac OS X, Mobile devices, Printers and any device with a local or public IP address. It is actually capable of simulating cyber attacks against systems so that they are better prepared for anything a hacker might have under his sleeve. In essence, the Penetrator will scan your device, network, or database to ensure that it is vulnerability-free.
Secpoint Penetrator Webadmin Interface
Most importantly, the SecPoint Penetrator is a device that evolves alongside security technology, so you'll never end up with an obsolete appliance that requires replacement post-haste. The reason for that is because the Penetrator regularly connects to the Internet in order to get the latest security updates around. Every time a new vulnerability is discovered, SecPoint databases are updated. The security company works round-the-clock in order to ensure that their products are always on top of the situation.
SecPoint Penetrator can be deployed as a:
• Physical hardware appliance.
• Virtual appliance (VMware or Hyper-V) .
• Cloud appliance.

Secpoint Penetrator Hardware Appliance